Last Updated on February 6, 2025
Protecting yourself online has never been more important. With more of your personal information online and cybersecurity attacks on the rise, it’s important to understand what cybersecurity risks exist and how you can protect yourself online.
It’s estimated that cybercrime will cause $10.5 trillion worth of damage annually.
Even more startling, an FBI agent who investigates cyber intrusions said, “Every American person should assume all of their data is out there.”
Let’s look at cybersecurity statistics in 2025, types of cyber attacks, and tips to protect yourself online.
Cybersecurity Statistics
Let’s look at cybersecurity statistics from around the world.
- It’s been estimated that a hacker attacks every 39 seconds. That means by the time you are reading this, there likely has already been an attack somewhere in the world.
- Cybercrime costs are expected to grow by 15% per year between 2020 and 2025.
- The FBI reported 2,211,396 complaints of internet crime between 2016 and 2020.
- Investment scam losses were estimated to be $4.57 billion in 2023.
- The FBI reported $12.5 billion in losses in 2023.
- In 2023, the FBI reported over 2,412 complaints received per day on average related to internet crime.
- People over age 60 were the most common victims with total losses over about $3.4 billion in 2023.
- Over 93% of healthcare organizations experienced a data breach between Q3 2016 and Q3 2019.
- 57% of healthcare organizations had more than five data breaches between Q3 2016 and Q3 2019.
- The FDA had a voluntary recall of 465,000 pacemakers in 2017 due to fears about hacking.
- 92% of people know that using the same password or variation is a risk, but 65% always or mostly still use the same password or variation, Lastpass reported in their Psychology of Passwords Survey.
- Social Security numbers can be purchased for $1, credit or debit cards for $5 to $110, and driver’s license for $20, according to Experian.
- Microsoft invests about $1 billion in cloud security each year.
- In 2021, Microsoft committed to spending $20 billion on cybersecurity, and Google committed to spending $10 billion over the next five years.
If you become a victim of a cybersecurity attack, it can be life changing and costly. Let’s look at the total losses by states.
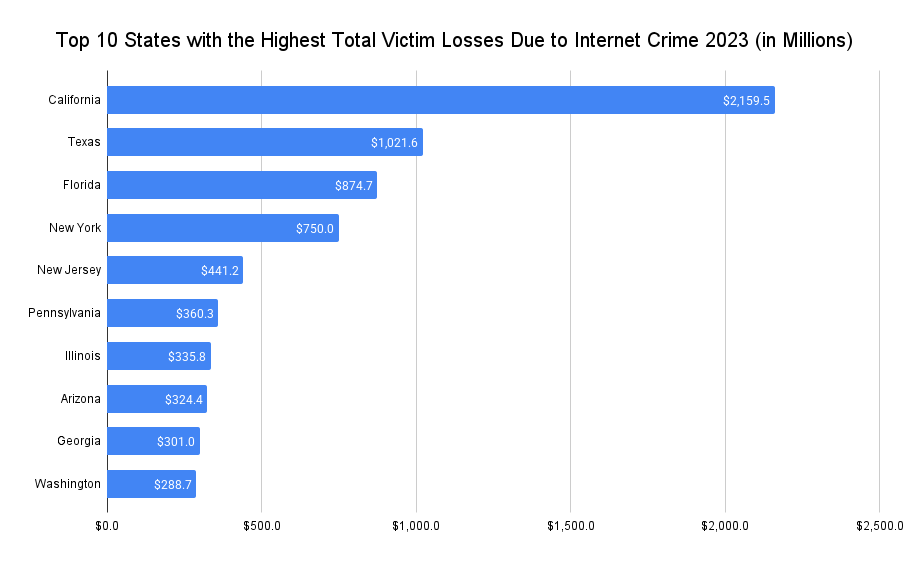
The Top 10 States with the Highest Total Victim Losses
- California
- Texas
- Florida
- New York
- New Jery
- Pennsylvania
- Illinois
- Arizona
- Georgia
- Washington
Notorious Data Breaches and Hacks
You can set up as many precautions as possible, but it’s important to remember that if a hacker wants your information, they likely can get it, which is why it’s important not to reuse passwords, set up two factor authentication whenever possible, and take other steps to mitigate access to your information.
Below are notorious data breaches. As you can see, these are large companies with some of the best resources in the world and very large security budgets, and they are still hacked.
- About 147 million people were affected by the Equifax breach in 2017.
- About 57 million Uber users were affected by an Uber breach in 2017.
- Uber tried to cover up the hack instead of reporting the stolen data as required by law. They paid $148 million to settle the claims.
- A hack on Yahoo in 2013 affected all three billion of Yahoo’s user accounts.
- Gary McKninnon allegedly hacked into 97 US government computers, some at the Pentagon, in 2001 and 2002.
- Saudi Aramco, which supplied about 10% of the world’s oil when it was hacked in 2012, had to physically unplug the internet at every office, gave away oil for free to keep it flowing, and bought over 50,000 hard drives until its network could be brought back up.
- Citigroup was hacked in 2011 and had the financial data of more than 360,000 customers revealed.
- Mt. Gox, a bitcoin exchange, was hacked and had the equivalent of $460M stolen from customer accounts.
- Colonial Pipeline was hacked in 2021 and showed the fragility of our critical infrastructure.
- Facebook was hacked in 2019, and 533 million Facebook users had their personal information exposed.
- Background check company National Public Data (NPD) suffered a breach in 2024 that caused 2.9 billion people to have their information leaked online.
Unfortunately, data breaches are common. Your information is likely out there.
Common Types of Cyber Attacks
Let’s look at common types of cyber attacks to make you aware of how a hacker might hack your information.
Romance Scams
Romance scams involved a criminal using a fake online identity to gain someone’s trust, often giving the illusion of a romantic relationship, in order to manipulate them. Usually, there is a plea for money starting in small amounts until it builds to much larger amounts — sometimes stealing someone’s entire bank account.
In 2023, it’s estimated that romance scams caused $652,544,805 in losses, according to the FBI’s 2023 Internet Crime Report. It was the fifth highest cause of loss.
The elderly are particularly susceptible to these types of scams because they are often not as familiar with technology, social media, and the scammers are extremely good at building trust.
Malware
Malware is software that is designed to damage or gain access to a computer system.
Below are seven types of malware:
- Virus
- Worms
- Trojan virus
- Spyware
- Adware
- Ransomware
- Fileless malware
Most people are familiar with viruses, which are often embedded in a document or file that executes code once the file is opened. Viruses normally cause data loss or make a system unusable.
Spyware is dangerous because instead of damaging a computer or disrupting it, spyware hides in the background to steal sensitive information and sends it to another person. A common type of spyware is a keylogger, which records your keystrokes, which can reveal passwords, bank account information, Social Security numbers, and more.
Ransomware is becoming more prevalent. It encrypts information within a system so that a user cannot access it. Then, it demands a financial payout, often in hard to trace payments, such as cryptocurrency or gift cards. Once paid, sometimes the data is unlocked.
Phishing
Phishing is where a cybercriminal will mimic or pose as a reputable company in order to get someone to reveal personal information, go to a malicious website, or open a malicious attachment.
Phishing attempts usually come via email. You may receive an email that appears to come from a company where you have an account, and the email invites you to click a link where you put in a password. Then, that information is stolen and used to gain access to your account.
The link might also go to a website where adware or ransomware is installed on your computer.
Although phishing attempts often come via email, they can also come through social media messages, text messages, misleading websites, and even phone calls.
Microsoft, Apple, and Google were the top three brands criminals attempted to mimic, according to IBM Security X-Force.
Phishing attacks often create a sense of urgency. They might say you are losing access to a financial account, a family member was injured in an accident, or you only have a limited time to respond.
Man-in-the-Middle (MitM) Attacks
A man-in-the-middle attack is similar to eavesdropping and uses phishing.
For example, a cybercriminal may email you asking you to login to your bank, but the link points to a website that looks just like your bank’s website, but isn’t. When you input your login credentials, the cybercriminal grabs them and then has access to your account.
Another type of MitM attack would be a hacker making a free, malicious WiFi hotspot. When you connect to the hotspot, the hacker can see your online data.
Password Attack
A password attack is where a hacker accesses a person’s password. The method of gaining access might include guessing the password, gaining access to a database containing passwords, or using common passwords.
In a study that Microsoft did in 2019, they found 44 million accounts were reusing the passwords found within a breached credential database.
It’s critical to not reuse passwords as it is likely only a matter of time until a password is breached. If you reuse passwords, you are inviting criminals to use those breached passwords on multiple websites.
It’s like putting a key outside of your door that also unlocks your bank account, car, medical records, credit card, and social media.
Tips to Protect Yourself Online
Knowing that major companies are breached every year and your information is likely online somewhere, what do you do?
How do you protect yourself online from identity theft, fraud, and other attacks?
Be Suspicious
It’s unfortunate you need to be suspicious of others, but it really is a good defense mechanism. You should be suspicious of unexpected phone calls, voicemails, emails, and text messages.
If you receive a call from an unexpected phone number, I normally recommend calling back the company with a publicly known phone number. For example, if your bank calls you asking for your date of birth or other information, you can hang up and call them back.
If someone says your computer has been hacked and they are computer support, you can do a quick internet search to see if it’s a common scam (it often is) or contact support through Apple, Microsoft, or another computer software provider to see if it is legitimate.
You don’t want to become a victim of elder financial exploitation.
For emails, it’s best to hover over links in your email to see where the link actually goes. Unfortunately, many phishing attempts come via email where the hacker wants you to click an attachment or a link that may install malware on your computer. If a bank emails you asking you to login, instead of clicking the link in the email, login online as you normally would. You can also call them to confirm the email you got is correct.
Also, hover over someone’s email address. It’s not uncommon for a hacker to impersonate another person’s email address, but if you hover over it, you can often see the real email address. Look at it closely because it might be just one letter that is off.
If you get a notice about anything being urgent or a family member being in trouble, your red flag should immediately go up. Scammers love to play to your emotions by creating a sense of urgency. They often impersonate another authority figure, such as a police officer or doctor. It’s okay to hang up and call the family member or someone else in your family to ask if they are okay. You may find out they are fine and surprised someone is impersonating them.
Two-Factor Authentication
Whenever possible, you should enable two-factor authentication for websites. As talked about earlier, it’s easy to get passwords from breached data. If you set up two-factor (or two-step or multi-factor) authentication, you are making it that much harder to login to your website.
Once you input your password, you may have to type a string of digits from a security app, text message, or phone call.
While it’s not foolproof, it is another barrier.
Use a Verbal Password
Many banks allow you to set up a verbal password that you need to say when you call. It’s another layer of protection.
In a world where your date of birth, Social Security number, and other private data is online, it may be possible for someone to use that information to call in and verify themselves as you.
A verbal password can be a random word that may not be easily identifiable and is usually not in a database associated with your private information.
Use the Phone
It’s much harder to impersonate a voice on the phone. If you ever receive a questionable online message or someone claims they can’t talk on the phone, call them using a known number – not the number in an electronic message.
It’s difficult to know who sent you a text message or email, but if you call someone, you can hear their voice, increasing the odds you can identify something as legitimate or as a fake.
Update Your Technology
When your computer or phone notifies you of legitimate updates, don’t wait to update them.
This could be for a browser, like Microsoft Edge, Safari, or Google Chrome, operating systems, or software.
Some updates are not improvements, but to fix security issues. If you wait days, weeks, or months to update your device, you may be leaving yourself vulnerable to a hack.
Don’t Use Public Networks
Public networks are not very secure. Whether you are in a coffee shop, at the airport, or in a hotel, you may be tempted to connect to the WiFi, but if you do, you are opening yourself up to being hacked.
Anything you do on that public network could be seen, such as credit card information, emails, and passwords.
If you are connected to a public WiFi connection, you should assume everything you are doing can be seen.
Many security experts recommend using your phone as a mobile hotspot to connect another device to the internet.
If you absolutely need to connect to a public WiFi network, many cybersecurity experts suggest using a VPN. The VPN will encrypt your data, making it harder to hack you.
Create Strong, Unique Passwords
Too many people reuse passwords or slight variations of passwords across websites.
You want to use a secure, unique password on each website that doesn’t include a date of birth, pet name, family name, or anything else that is easily identifiable to you.
Ideally, it would be a long password with a combination of characters, numbers, and symbols.
I realize most people can’t remember a long password that is unique to each website, which is why some security experts recommend using a password manager to create and store passwords.
Instead of needing to remember 30+ passwords on multiple websites, you only need to remember one secure and unique password to access the password manager. Then, the password manager can fill any of your online passwords for you.
Final Thoughts – My Question for You
The cybersecurity statistics are startling.
Companies spend billions of dollars on cybersecurity and are still hacked. The FBI receives thousands of complaints of internet crime per day. People are still reusing passwords despite how dangerous it can be.
In a world where data breaches are common for corporations, and it’s easy to become the victim of a phishing attempt, it’s important to remember tips to protect yourself online.
- Be suspicious
- Use two factor authentication
- Use a verbal password
- Use the phone
- Update your technology
- Don’t use public networks
- Create strong, unique passwords
I’ll leave you with one question to act on.
How are you going to improve your cybersecurity today?





